CompTIA Pentest Challenge 2: Basic Brute Forcing Practice
CompTIA Pentest Challenge 2.
This time we're doing some basic password brute forcing involving FTP, SSH, MySQL and HTTP. Login IDs, service types and a dictionary of known passwords are provided. If the IP addresses change in the screenshots it's because I had to stop to do something halfway through!
First we have to guess the FTP password of user "jimmy". Let's get thc hydra going and point it to our password dictionary.
Cool, batman, an interesting selection. Let's login over ftp.
It works! Let's see what's here using ls.
There's the token, let's get it with get!
Cool, we've got it. Let's check out the file.
Done. Time to start on the SSH user "bob".
Pretty similar to the first brute force, but changed the username and service.
The password's "sunshine", so let's login to SSH.
We're in! I guess it'll probably be the same as the last one, so let's see what files are around.
It was the same! Here's the token.
Let's move to MySQL with user "root", the process for this one will be a bit different than the past 2. There is additional info explaining the token will be in the "tokens" database.
First we'll get the password using hydra like before, again changing the user and service.
Password is "letmein", that's how i feel too.
This is where it's a bit different. We need to be able to get a connection to the server to be able to manipulate MySQL, so let's login to SSH as bob from before.

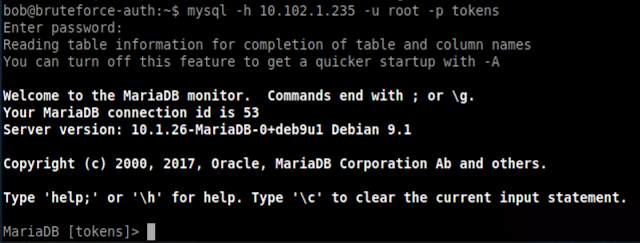
We're in! Again! Let's login to the "tokens" database as root.
Made it into the database. Let's use some SQL commands to snoop around and find the token.
I used SHOW to show all tables in the "tokens" database. It turns out there's one table, also named "tokens".
I used SELECT * to select all entries in the table. I assumed there was probably only one entry in the table. Let's go to HTTP to guess the password for "rupert".
So this one has additional info telling us to target the "secrets" page specifically. This part is (probably?) the easiest because everyone is familiar with logging in over HTTP. Let's do the hydra thing.
Ok, password. Didn't even need hydra lol.
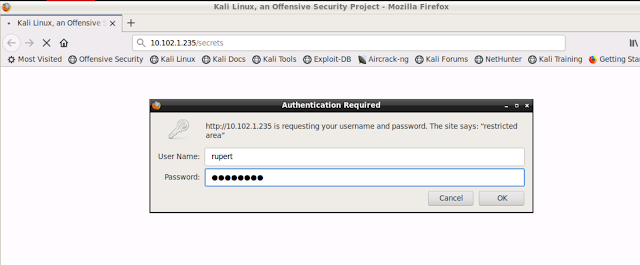
Time to open up firefox, go to the site and login.
We're authenticated as "rupert" and the token is displayed on the page.













I get incredible information in your blog.
ReplyDelete